A future-proof money system
Now that we have explored the first principles of trust, money and decentralisation, what does a concept based entirely on these principles look like?
Most importantly and as described above: Such a system should encourage operators to reveal their identity and allow users to select their trusted operators in the system.
From now on, we will refer to trusted operators as trustees, because they take on tasks such as keeping identities, accounts, contracts and other data confidential, processing transactions, storing data, hosting applications and much more.
However, technically, it is simply a replicated database, and all operators must agree on the most recent state on a regular basis. Because trust is the foundation of this system, the community’s values include honesty and integrity. And any operator who violates these values will be banned. Operators can update whatever they want in the database, but as soon as they try to broadcast fraudulent messages or modifications, the honest operators will blacklist them.
We feel that a separate name for this technology is required because the way it operates is fundamentally different from blockchain technology and the term ‘ledger’ in DLT is insufficient to cover all areas of possible use.
In essence, it is a type of interconnected computer network, similar to the internet, but based on trust. As a result, we propose the name: Trustnet.
Just as Satoshi proposed the first blockchain-based solution with Bitcoin, we would also like to propose a first concept based on trustnet technology.
The project is called Trusdee.
Trusdee is a highly modular system. These modules are called DApps (just like in the blockchain ecosystem), but work differently than in current DLT solutions. For instance, they should not be confused with smart contracts, as these are executed sequentially and the same computing operations must be repeated by all nodes. This severely limits the scalability of smart contracts, which is why they should only be employed in a trustnet where a time-dependent sequence of computational operations is unavoidable.
Trustnet DApps, on the other hand, are fully decentralised applications that are executed asynchronously and nodes may have to perform different tasks. This has the advantage of allowing DApps to scale with the trustnet without suffering performance degradation.
In addition, unlike blockchain DApps, trustnet DApps do not consist of smart contracts as a backend and individually hosted frontends, but are bundled applications that contain both the backend (source code executed by the nodes) and the frontend (source code executed by the client). This opens up a whole new world of possibilities.
There are numerous advantages to using a modular system, including:
DApps can be developed and updated independently of one another without interfering with other DApps. This is crucially important, for example to keep the whole system around the money module up-to-date, without touching the money module or changing the monetary policy of the system.
Users can choose which DApps they wish to utilise and which they don’t. This means, for example, that if a user does not require or wish to use the Identification DApp (described in detail in the next section), they can simply ignore it.
As with a free market economy, there is a free market of DApp solutions. This means, for example, that there may be multiple competing DApps for smart contracts (each with its own set of features and characteristics), with the best variant having the best chance of succeeding in the long term.
The only exception is the Digital Commodity Money DApp (which we will come back to later).
Trusdee without any DApps is simply a decentralised hosting platform that has no end-user functionality. For this reason, the Trusdee project will include the following DApps by default:
Digital Commodity Money, aka Cryptocurrency (Trusdee’s native money with the characteristics mentioned above)
Decentralised Exchange (marketplace to trade in and between all digital assets on the platform)
Smart Contracts (programmable self-executing contracts)
Public & Private Data Storage (‘public’ for digital asset ownership and ‘private’ for an encrypted cloud vault)
Decentralised Identity Registry (trusted sensitive data storage)
Decentralised Name Service (memorable names for users, applications and digital assets)
Another reason why Trusdee has standard DApps is that these functionalities are fundamental to any decentralised platform and third-party DApps are heavily dependent on them. If all third-party DApps are deeply integrated with the standard DApps, it increases compatibility between DApps, which greatly increases the usefulness of the entire platform.
We will publish the Trusdee white paper describing all the technical processes in detail in the next few weeks, but here is a simplified overview of how Trusdee works:
As previously stated, any individual, organisation, or company can participate in the operation of Trusdee. And operators are free to reveal or hide their identity as they choose.
Users must first choose seven trustees before they can use the Trusdee platform. They can, of course, change their trustees at any time. If users provide personal information, it will only be maintained by their trustees. Furthermore, transactions done by a user can only be linked to that user by their trustees.
Aside from the last 3-6 hours of data, no historical data is retained in the system by default. This means that a user does not have a transaction history by default, but must explicitly instruct his Trust-Nodes on how long they should keep the data of previous transactions. Not only the transaction history, but also data such as public digital assets, encrypted private data, a user’s smart contracts, and so on, are solely maintained by the respective Trust-Nodes, and only the fingerprint (hash) of the corresponding data is broadcast to the entire network. This reduces the network’s storage requirements to a basic minimum.
Another advantage is that transactions do not need to be pooled before being published as blocks at regular intervals. Instead, they only need to be verified by the sender’s and receiver’s Trust-Nodes before being broadcasted. If one or more nodes broadcast an invalid transaction (or, more broadly, an invalid change to the overall state), the honest nodes commence a blacklisting procedure. If the broadcasting node cannot show that the state change propagated is valid, it will be barred from participating in the system’s operation by the honest nodes.
This also has the advantage of not mattering how many nodes an attacker has, because all nodes that are not honest will be excluded from participating in the operation regardless of the number of nodes. Strictly speaking, this is a mutual exclusion, as nodes cannot distinguish between honest and fraudulent nodes, but can only check whether the rules programmed into their software have been followed. Nodes do not know whether their software has been tampered with or not, and therefore fraudulent nodes blacklist honest nodes the same way honest nodes blacklist them.
As a result, the trustnet splits into two separate trustnets (similar to how hard forks happen on blockchains). However, in order to create a new trustnet, at least 7 nodes must be involved. This means that even if there were only seven honest nodes in the network, the security of the trustnet would be guaranteed since these nodes would form a new trustnet after a network fission and users may choose them as their new Trust-Nodes. This gives a trustnet a Nakamoto Coefficient of , where .
The Nakamoto Coefficient is a measure of how decentralised a particular subsystem of a DLT solution is and was first introduced by Balaji Srinivasan in his article Quantifying Decentralization.
This basically means that the only way a user could be defrauded in a trustnet would be if all of his Trust-Nodes were traitors and were conspiring against him. But in that case, the user should question his discernment.
As mentioned above, Trusdee does not use a blockchain as a database of all data. All information concerning state transitions is transient, and only the most recent state is saved. Data storage is handled by well-known and high-performance DBMSs.
However, in a few cases Trusdee uses blockchain technology to solve technical challenges. For example, the assent of all nodes to the latest state is recorded every 3-6 hours in a block of a blockchain. That block contains the fingerprint (hash) of the previous block, the Merkle hash root of the current state and the signature of all nodes.
Since each block contains the signatures of all nodes, it is sufficient to store only the last block (of course, nodes can still store several blocks or even the entire blockchain (history of the network state’s fingerprint)). This feature of Trusdee makes it possible to reduce the storage requirement to nearly the theoretical minimum.
And, by reducing the bandwidth, storage, computing, and memory capacity requirements to a basic minimum, we not only enable very low-cost participation in the system’s operation (which, by the way, ensures a high level of decentralisation), but also significantly reduce the overall network’s energy consumption. As a result, we may avoid the never-ending energy consumption debates, judgmental studies, discussions and governmental attempts at intimidation.
In terms of fairness, a trustnet’s system integrity mechanism outperforms all existing consensus mechanisms. People with a lot of money have a clear edge under the existing systems, whether they are purchasing mining hardware or staking tokens.
With a trustnet’s system integrity mechanism reputation is at stake, and it is almost impossible to buy a good reputation. This means that, regardless of financial resources, everyone has about equal odds with Trusdee, because anyone can build up a wide reach on the internet these days. As aforementioned, it is quite difficult to establish a good reputation and maintain it over a long period of time, but fairly easy to destroy it quickly. Thus, only the truly trustworthy participants will emerge in the long run. As a result, it is the best way to prevent anyone from gaming the system.
Trusdee not only resolves the Blockchain Trilemma, but also a whole host of other DLT-related issues:
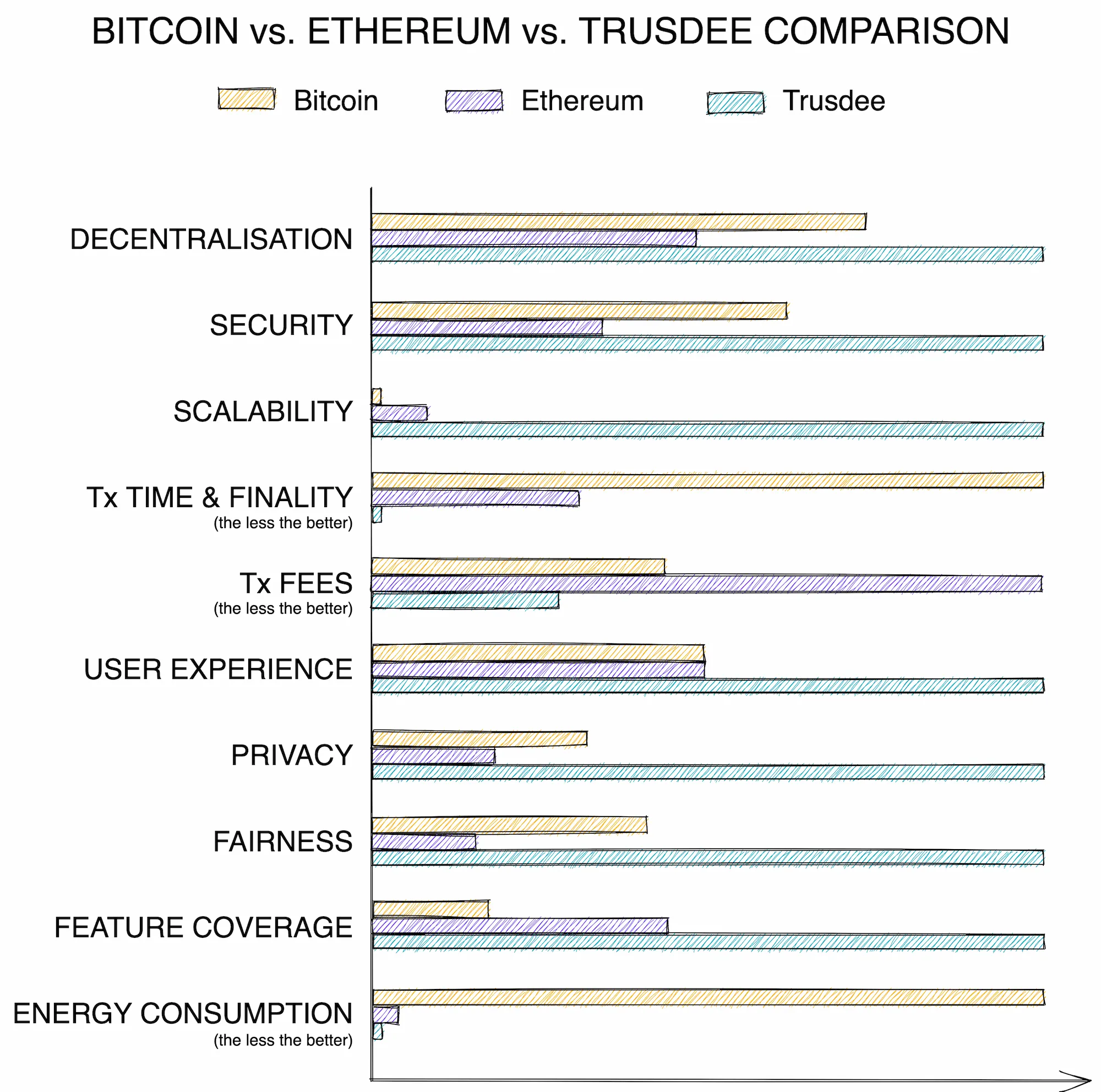
* Tx = Transaction
We are aware that these values are subjective estimates, but it provides a rough indication of Trusdee’s potential.
So far, no other technology on the market has managed to achieve this combination. Furthermore, a trustnet eliminates practically all of Bitcoin’s (and other blockchain solutions) other weaknesses without introducing any new ones (at least none that we can identify).